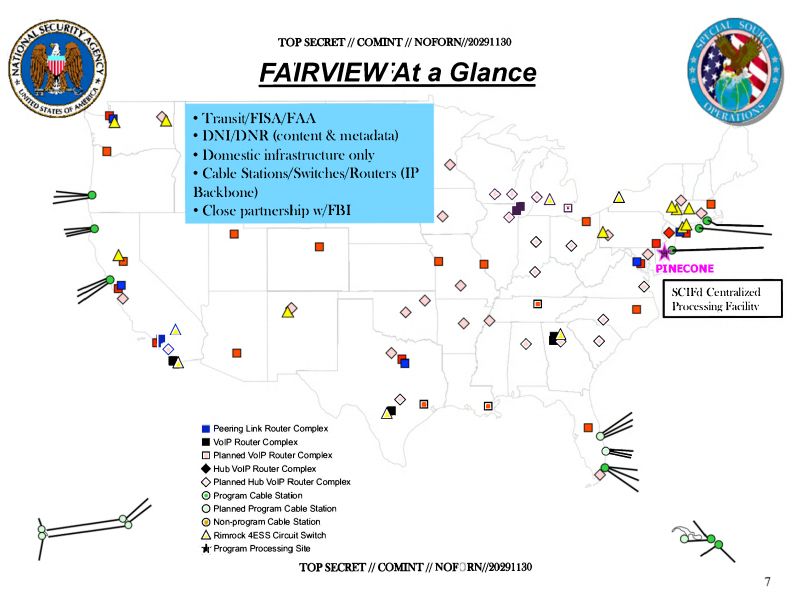
Two departments of the US federal government may have spent as much as $21 trillion on things they can’t account for between 1998 and 2015. At least that’s what Mark Skidmore, a Professor of Economics at MSU specializing in public finance, and his team have found.
They came up with the figure after digging the websites of departments of Defense (DoD) and Housing and Urban Development (HUD) as well as repots of the Office of the Inspector General (OIG) over summer.
The research was triggered by Skidmore hearing Catherine Austin Fitts, a former Assistant Secretary in the HUD in the first Bush administration, saying the Inspector General found $6.5 trillion worth of military spending that the DoD couldn’t account for. She was referring to a July 2016 report by the OIG, but Skidmore thought she must be mistaking billion for trillion. Based on his previous experience with public finances, he thought the figure was too big even for an organization as large as the US military.
“Sometimes you have an adjustment just because you don’t have adequate transactions… so an auditor would just recede. Usually it’s just a small portion of authorized spending, maybe one percent at most. So for the Army one percent would be $1.2 billion of transactions that you just can’t account for,” he explained in an interview with USAWatchdog.com earlier this month.
After discovering that the figure was accurate, he and Fitts collaborated with a pair of graduate students to comb through thousands of reports of the OIG dating back to 1998, when new rules of public accountability for the federal government were set and all the way to 2015, the time of the latest reports available at the time. The research was only for the DoD and the HUD.
“This is incomplete, but we have found $21 trillion in adjustments over that period. The biggest chunk is for the Army. We were able to find 13 of the 17 years and we found about $11.5 trillion just for the Army,” Skidmore said.
The professor would not suggest whether the missing trillions went to some legitimate undisclosed projects, wasted or misappropriated, but believes his find indicates that there is something profoundly wrong with the budgeting process in the US federal government. Such lack of transparency goes against the due process of authorizing federal spending through the US Congress, he said.
Skidmore also co-authored a column on Forbes, explaining his research.
The same week the interview took place the DoD announced that it will conduct its first-ever audit. “It is important that the Congress and the American people have confidence in DoD’s management of every taxpayer dollar,” Comptroller David Norquist told reporters as he explained that the OIG has hired independent auditors to dig through the military finances.
“While we can’t know for sure what role our efforts to compile original government documents and share them with the public has played, we believe it may have made a difference,” Skidmore commented.
Interestingly, in early December the authors of the research discovered that the links to key document they used, including the 2016 report, had been disabled. Days later the documents were reposted under different addresses, they say.
Source: $21 trillion of unauthorized spending by US govt discovered by economics professor